Enhancing Security and Reliability: The Vital Role of Dedicated Proxies
 By
By
In today's digital
landscape, where online activities encompass everything from personal
communication to business transactions, ensuring security and reliability is
paramount. One key tool in achieving this goal is the use of dedicated proxies.
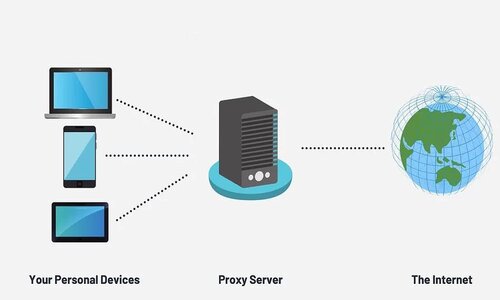
These specialized servers act as intermediaries between users and the internet,
offering a range of benefits that enhance security, privacy, and reliability.
Understanding the importance of secure and reliable dedicated proxies is
essential for businesses and individuals alike. Types of Dedicated
Proxies Dedicated
proxies are secure and
reliable, so you're not just obtaining IP addresses but also attaining project
success. Dedicated ISP proxies and dedicated data center proxies are two
distinct types of proxy servers used for anonymity and accessing restricted
content. Dedicated ISP proxies
are provided by Internet Service Providers, utilizing residential IP addresses
assigned to individual users. They offer reliability, better IP reputation, and
mimic natural user behavior, making them suitable for tasks requiring high
anonymity. In contrast, dedicated data center proxies operate from data center
facilities, using IPs provided by hosting providers. They are faster and
more cost-effective but face higher detection rates by websites due to their
association with data centers. Dedicated ISP proxies excel in tasks like web
scraping and social media management, while dedicated data center proxies are
preferable for web browsing and price comparison. Despite ISP proxies'
better anonymity, both types may encounter detection and blocking issues, with
data center proxies facing more scrutiny from websites. Therefore, choosing
between them depends on specific use cases, balancing factors like anonymity,
speed, and cost. When choosing between
dedicated ISP proxies and dedicated data center proxies, consider anonymity
needs, speed, IP reputation, cost, intended use, and detection risk. Assess
your priorities and tasks to determine which type best suits your requirements. Security breaches and
cyber threats are constant concerns in the digital realm. Dedicated proxies
play a crucial role in bolstering security by acting as a barrier between
users and potentially malicious entities on the
internet. By routing internet traffic through a dedicated proxy server, users
can conceal their IP addresses, making it difficult for cybercriminals to track
or target them directly. Moreover, dedicated
proxies offer encryption capabilities, adding an extra layer of security to
transmitted data. This encryption ensures that sensitive information remains
confidential and protected from interception or unauthorized access. Whether
conducting financial transactions, accessing sensitive company data, or simply
browsing the web, the security provided by dedicated proxies helps mitigate the
risk of data breaches and cyber attacks. Privacy concerns have
become increasingly prevalent in the digital age, with users seeking ways to
protect their personal information from prying eyes. Dedicated proxies
contribute to privacy preservation by masking users' IP
addresses and obscuring their online activities. This anonymity prevents third
parties, such as advertisers or government agencies, from tracking and monitoring
individuals' online behavior without their consent. For businesses,
safeguarding customer data is of utmost importance to maintain trust and
compliance with privacy regulations. By utilizing dedicated proxies, companies
can ensure that sensitive customer information remains confidential and
protected from unauthorized access. This not only fosters customer trust but
also helps businesses avoid potential legal repercussions associated with data
breaches or privacy violations. Facilitating Reliable
Connections In addition to
security and privacy benefits, dedicated proxies offer reliability in internet
connectivity. By utilizing dedicated servers with high-speed connections, users
can experience faster and more stable internet access, particularly in
scenarios where network congestion or geographic restrictions may hinder
performance. This reliability is especially crucial for businesses that rely on
consistent internet connectivity to conduct operations efficiently. Moreover, dedicated
proxies enable users to bypass geo-blocking restrictions imposed by certain
websites or online services. This capability allows individuals and businesses
to access content and services that may be restricted based on their geographic
location, enhancing convenience and flexibility in online activities. Conclusion The importance of
secure and reliable dedicated proxies in today's digital landscape cannot be
overstated. These specialized servers play a vital role in enhancing security,
safeguarding privacy, and facilitating reliable internet connections for both
individuals and businesses. By concealing IP addresses, encrypting data, and
providing reliable internet access, dedicated proxies empower users to navigate
the online world with confidence and peace of mind. Whether protecting
sensitive information, preserving privacy, or accessing geo-blocked content,
the benefits of dedicated proxies extend across various aspects of online
interactions. As cyber threats continue to evolve, integrating dedicated
proxies into digital strategies is essential for mitigating risks and ensuring
a safer and more secure online experience for all.Enhancing Security
Safeguarding Privacy






